Virtualization and container technologies are confusing topics in their own right, and comparing and contrasting them is even harder. To understand the differences between container and virtualization technologies, it’s best to clear up some commonly misunderstood information on how they work. Containers are made up of the bare minimum hardware and software requirements to allow […]
Author Archives: Jeff Bolden
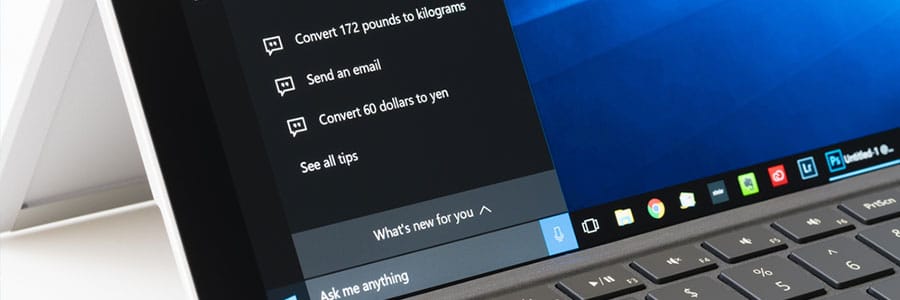
You’ll find Cortana, Microsoft’s voice-activated personal assistant, extremely helpful for daily tasks, like rescheduling meetings, drafting an email, or dealing with several other time-consuming work. Learn how to use the following Cortana commands to make life so much easier for you. Hey, Cortana Before asking her to do anything, we need to get Cortana’s attention […]
Do you spend hours obsessing about the inner workings of DNS-layer security, intrusion prevention systems, and data encryption? If you’re not a managed IT services provider (MSP), you probably don’t. Instead, you’re probably looking for a business partner to manage those nitty-gritty details for you. However, there’s one thing you really ought to know: What […]
If you’re a Mac user, data privacy and security should be your #1 priority. Without the right security measures, you’re inviting cybercriminals to steal your critical data. Are you willing to take the risk? Secure your computer and fortify your defenses with these six tips. The basics First, let’s start with the basics and head […]
The Internet of Things (IoT) is a network of vehicles, appliances, and devices embedded with actuators, connectivity, software, electronics, and sensors that allow users to connect and swap data. The business world is steadily changing with the implementation of IoT in the following methods. Improved logistics With IoT sensors, supply chain management and order fulfillment […]
Moving to the cloud can save you a considerable amount of money, which explains its rise in popularity over the years. What many business owners fail to realize is that some cloud services come with hidden costs. And while they might seem insignificant at first, they can add up to a staggering amount if left […]
Although Windows 10 is packed with wonderful new features, it’s far from perfect. Users have complained about storage, connectivity, and update issues, among other things. If you’ve encountered any of these issues, no need to panic. We have listed down five simple fixes to the most common Windows 10 problems. 1. Less storage space When […]
As a small- or medium-sized business (SMB) owner, you need to stay on top of IT trends to get ahead. However, many new IT solutions are quite confusing. One of those is app virtualization. To clear up the confusion, here is a quick overview of what it’s all about. What are non-virtualized apps? To understand […]
Ever wonder why Google goes through all the trouble of remembering your searches and online shopping history? It’s not only for the company’s benefit, but also to make tasks and scheduling easy for you. By predicting work patterns and files that you are more likely to use, something called machine learning boosts your productivity. Based […]
When it comes to cyberattacks, most business owners get hung up on the technical and logistical details, forgetting another important aspect: motive. Why are hackers attacking people and organizations? And whom are they targeting? By answering these questions, you’ll have a better understanding of which of your business’s resources need the most protection. Script Kiddies […]